If you're a healthcare startup, you're likely feeling the pressure of compliance requirements. But as stressful as it gets, compliance is also a core building block for your company and a crucial prerequisite for funding and market success. HIPAA (Health Insurance Portability and Accountability Act) compliance, in particular, is non-negotiable for companies operating in the U.S. healthcare system that handle protected health information (PHI).
As a healthcare software development company with 15 years of experience, we’ve helped U.S. startups develop HIPAA-compliant web and mobile applications — so we know the challenges first-hand. That’s why we’ve collected our battle-tested knowledge in this blog post to help you navigate the process of developing HIPAA-compliant software.
What is HIPAA compliance?
HIPAA compliance refers to the set of federal laws that establish rules for sharing personal medical information and protecting it from unauthorized use. In simple terms, the provision sets standards for healthcare providers, health plans, and healthcare clearinghouses (and their business associates) that handle electronic Protected Health Information (ePHI).
Now, let’s break down the key terms:
- Protected health information (PHI): any personal information about the patient or data about their health state that is held by a medical provider. PHI may include everything from names to lab tests.
- Covered entities: Clinics, doctors, insurers, and healthcare participants who transmit patient health information electronically in connection with certain transactions.
- Business associates: contractors that provide services to a healthcare provider in which PHI is disclosed.
- Business associate agreement (BAA): establishes a legally binding relationship between HIPAA-covered entities and business associates to ensure PHI is locked down.
Important organizations to know:
- HHS (Department of Health and Human Services): an organization responsible for developing and issuing HIPAA regulations.
- OCR (Office for Civil Rights): HIPAA's enforcer that will come knocking at your door if your compliance-subject app falls out of compliance.
HIPAA compliance isn’t a choice, and here’s why
Some healthcare companies, especially in their early days, tend to defer compliance, thinking they can catch up later. But this short-sighted approach can land your company in hot water.
Patient trust
Nearly 93% of patients want health app developers to clearly communicate their data handling practices and adherence to industry standards. If your application can't demonstrate compliance with HIPAA guidelines, patient users will understandably be hesitant to share their sensitive health information with an app that doesn't prioritize data security and privacy. In this case, they're likely to switch to a competitive, HIPAA-compliant product.
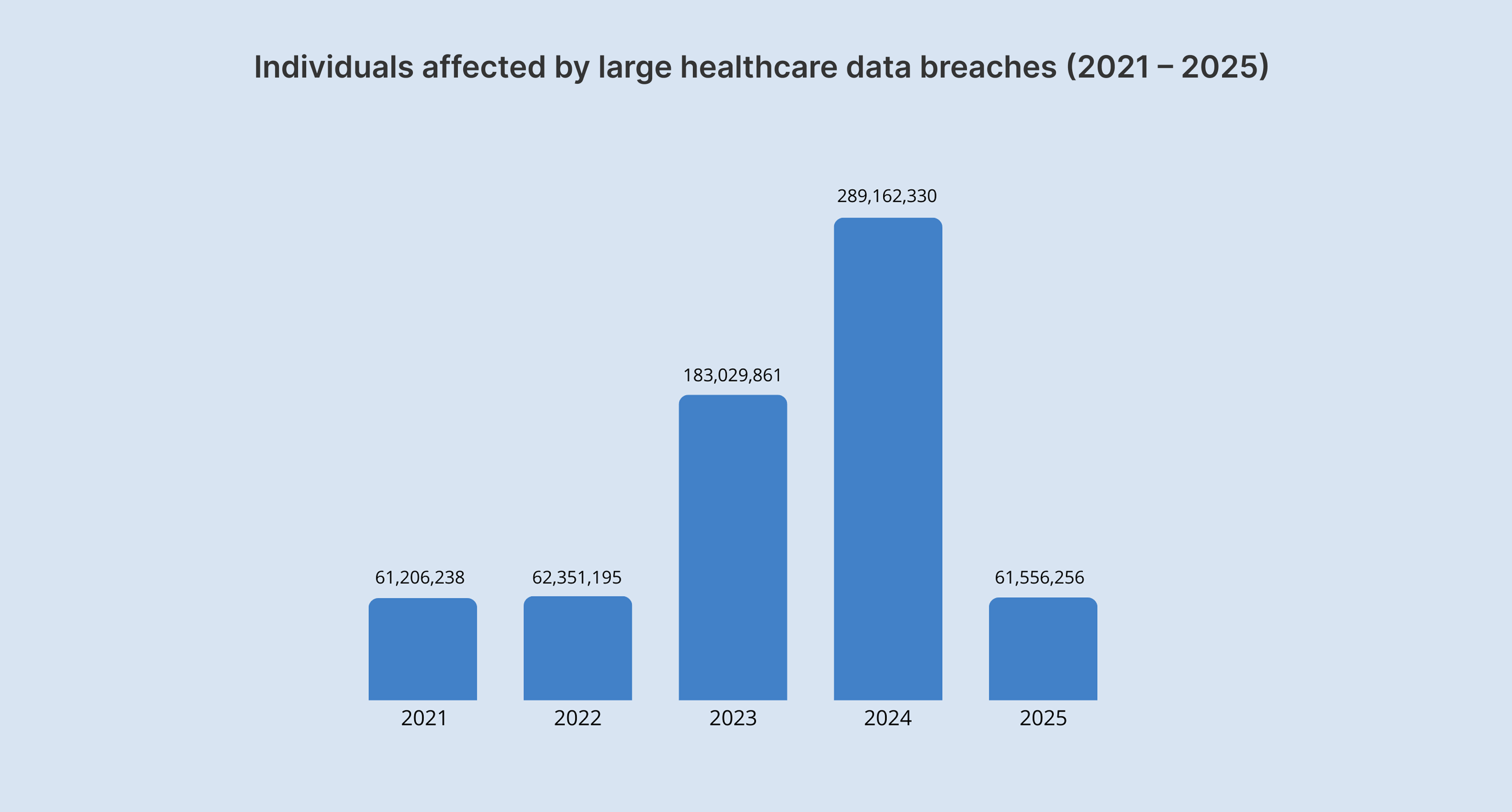
Healthcare provider trust
If you plan on promoting your healthcare mobile or web solution to hospitals, clinics, and other healthcare organizations, they need to be confident that your app and your company take patient data security threats seriously. If you can't demonstrate HIPAA compliance, you'll struggle to secure essential partnerships, which will likely undermine your business growth.
Hefty penalties
While some startups view compliance as expensive, they don’t realize how much non-compliance costs. The legal ramifications of having an app that falls out of compliance include enormous fines that can go up as high as $2,190,294 per violation, depending on the level of culpability. Mess with HIPAA on purpose, and you could be looking at up to 10 years in jail.
The year 2024 almost broke a record with more than $9.9 million collected in 22 settlements and civil monetary penalties, but six of the 22 enforcement actions were announced only in January 2025.
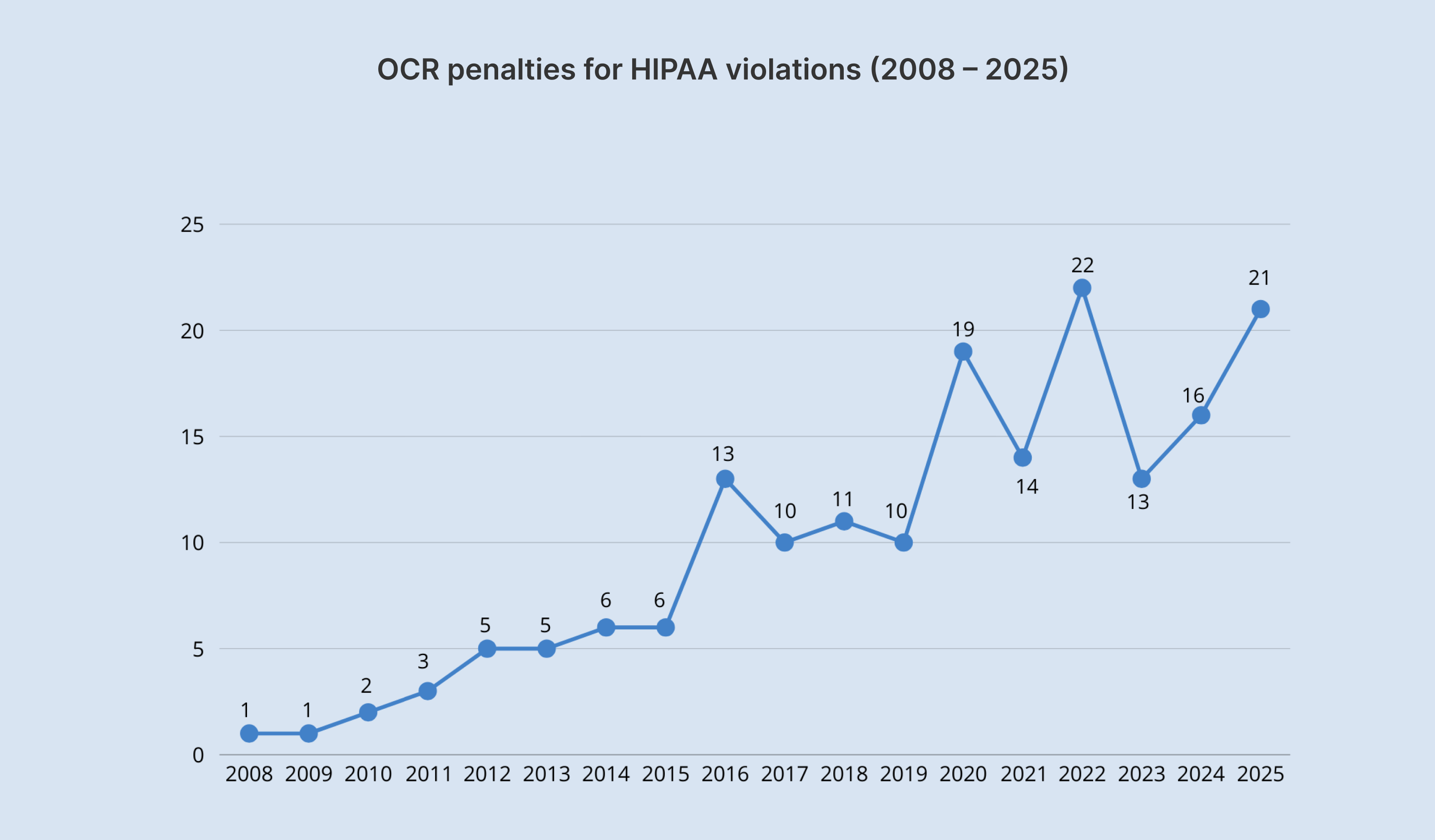
Unlike other laws, HIPAA has no safe harbor clause. So, if an organization has to do with PHI data, whether it wants to or not, it can’t opt out of HIPAA compliance.
Survival past series A
Healthcare is a heavily regulated space, and your potential investors are well aware of the fact that non-compliant healthcare products with PHI don’t stand a chance in the market. If you’re planning on pursuing funding, you need to have a clear and demonstrable plan for HIPAA compliance in place.
Are all healthcare mobile and web apps subject to HIPAA compliance?
If you’re venturing into the healthcare sector, it doesn’t necessarily mean your product is controlled by HIPAA. HIPAA requirements are triggered in specific cases, which include the following:
- Your software collects, uses, transmits, analyzes, or even just views PHI. It's not about the type of app but the data it processes.
- Your software doesn’t have to interact with patients directly. But if it's interacting with a covered entity or business associate and PHI is involved, HIPAA likely applies to you as a business associate.
- If a healthcare organization electronically transmits health information in connection with transactions such as claims, benefit eligibility inquiries, referral authorization requests, or other transactions, it makes them a covered entity under HIPAA.
What is considered Protected Health Information?
Any health information that provides insights into the past, present, and future health state of the user is ranked as PHI. Even seemingly non-health data, such as driver's license numbers or birth dates, can become PHI if combined with health information (e.g., "John Doe, DOB 01/01/1970, diagnosed with diabetes").
According to HIPAA Journal, the following specific 18 identifiers make your health information PHI:

However, if a user uses the application to monitor vitals such as body mass index (BMI) or heart rate, and the collected data is not sent to any covered entity or their business associate, this type of data is not bound by the act's requirements.
HIPAA compliance scenarios
Knowing whether the data is PHI is not always black and white. That’s why we’ve listed a few common scenarios so you can better understand what PHI is.
Offline tracking
A user records their blood pressure readings in a personal health tracking app on their smartphone. The app stores the data locally and neither transmits it anywhere nor shares it with covered entities.
📌 HIPAA compliance: Not required. Since the data remains on the user's device and isn't shared with a covered entity or their BA, it doesn’t fall under the definition of PHI under HIPAA.
Web portal for messaging
A patient communicates with their doctor’s office about their treatment plan, discussing their health condition, diagnoses, and treatment options. Messages are exchanged between the patient and the doctor via the web portal.
📌 HIPAA compliance: Required. This scenario is a textbook example of a PHI exchange between a patient and a covered entity.
Remote patient monitoring
A patient uses a smartwatch to track their heart rate and activity levels. The biometric data is then sent to a web platform monitored by a remote care team. The platform is provided by a third-party vendor.
📌 HIPAA compliance: Required. This scenario involves a covered entity (a remote care team), PHI (heart rate, health-related activity levels), and the transmission of PHI to a business associate (a third-party vendor). In this case, the BA and the covered entity are legally bound by a BAA.
Personal health dashboard
A user creates an account on a website and manually enters their weight, blood pressure, and diet information. The website tracks and visualizes this data without sharing it with any healthcare provider.
📌 HIPAA compliance: The dashboard doesn’t share any data with any healthcare provider, so the solution is not subject to HIPAA.
Fitness tracking
A company develops a fitness tracker app that tracks steps, heart rate, and sleep patterns. A hospital reaches out to the company, planning to provide the app to its patients as part of a wellness program.
📌 HIPAA compliance: Since the app developer is acting as a BA, data collected from patients is PHI, so HIPAA requirements are triggered. However, if the same app is published on the app store for individuals to download and use on their own, without sharing the data with a hospital, HIPAA requirements aren’t triggered — even if it's the same type of data.
Telemedicine platform
A company creates a telemedicine platform for virtual consultations. A clinic subscribes to the platform to provide telehealth services to its patients.
📌 HIPAA compliance: The clinic subscribing to the platform made the platform’s provider a BA, and the data exchanged during the consultations is PHI. In this case, HIPAA compliance is mandatory. If, however, the same company develops a separate, direct-to-consumer version of the platform where individuals can connect with doctors independently, without looping in a healthcare provider, the platform provider is likely not a BA, and the data shared may not be PHI under HIPAA.
Key elements of HIPAA
The Health Insurance Portability and Accountability Act comprises six core elements that together create a comprehensive framework for protecting health information. You can't adhere to one rule and ignore the others.
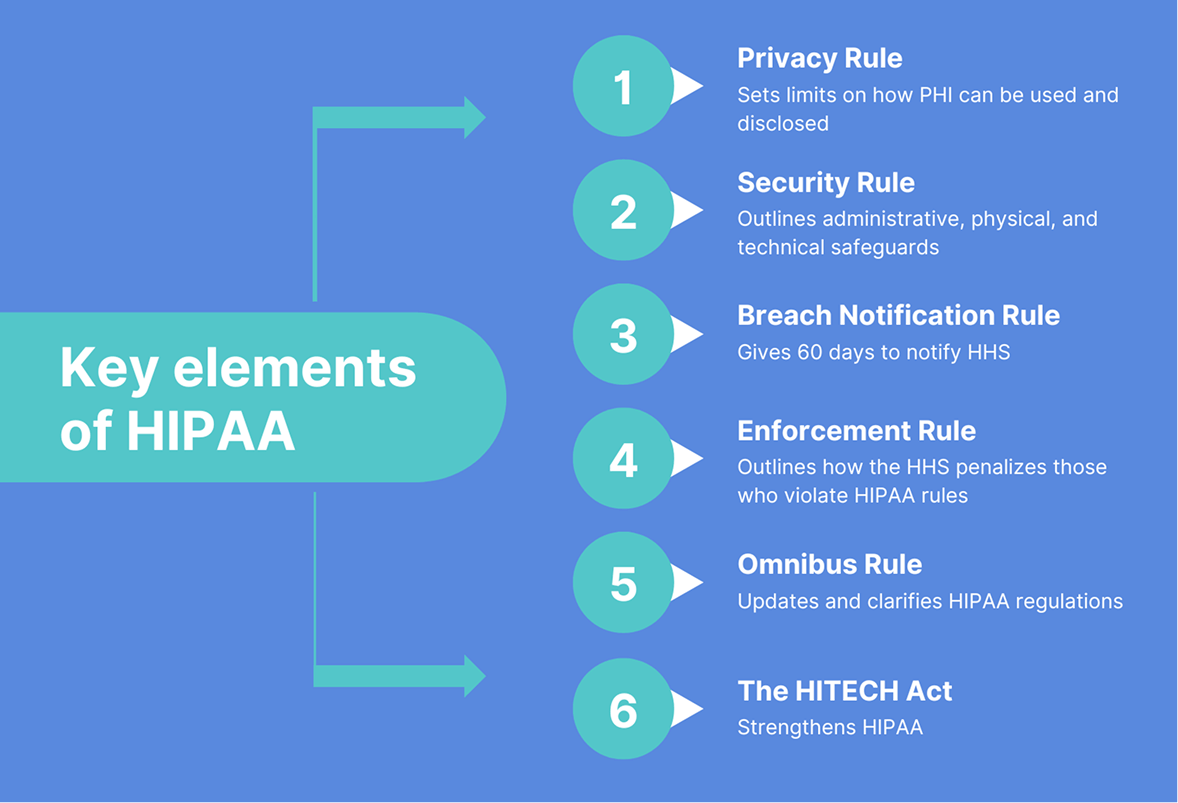
Privacy Rule
The HIPAA Privacy Rule lays out the standards for the use and disclosure of individuals' health information. It aims to strike a delicate balance between individual privacy rights and the need for data sharing to continuously improve the quality of care. The rule defines PHI, details permitted uses and disclosures, and grants individuals several rights with respect to their PHI.
💡Tip: This Rule provides a ‘workaround way’ to work with health information without it being PHI. According to the Privacy Rule, if health data is properly de-identified, it is no longer PHI and no longer falls under HIPAA rules.
Security Rule
The HIPAA Security Rule requires covered entities and their business associates to protect ePHI by adhering to administrative, physical (addressable/required), and technical (addressable/required) safeguards.
- Technical safeguards — these are the type of safeguards you need to implement when you’re developing a HIPAA-compliant mobile app or a web solution.
- Physical safeguards — these are the physical measures, policies, and procedures you need to implement to protect your IT systems, related buildings, and equipment from unauthorized access, tampering, and natural and environmental hazards.
- Administrative safeguards — these are the organizational and management aspects of HIPAA security.
Breach Notification Rule
The Breach Notification Rule is a federal law that requires organizations to notify individuals if their personally identifiable information has been compromised as a result of a data breach. If unsecured PHI slips through the cracks, the organization has 60 days to notify affected individuals.
Enforcement Rule
The Enforcement Rule introduces the ability of the Department of Health and Human Services (HHS) to investigate HIPAA violations, determine liability, and issue fines for non-compliance. Investigations typically stem from a complaint or a data breach, but HHS can also do random checks with no trigger involved.
According to the enforcement results, the HHS Office for Civil Rights has received over 328,000 HIPAA-related complaints since 2003.
The HITECH Act
Essentially an update to HIPAA regulations, the HITECH Act promotes the adoption and meaningful use of electronic health records (EHRs) by healthcare providers, plus pushes for their interoperability. The HITECH Act also made third-party vendors (business associates) directly liable for following HIPAA.
The Omnibus Rule
The Omnibus Rule updates and clarifies HIPAA regulations while also incorporating changes from the HITECH Act. It strengthens privacy and security rules, enhances data breach notification requirements, reinforces business associate liability, and addresses the potential gaps in various aspects of the Privacy, Security, and Enforcement Rules.
Your checklist for HIPAA-compliant app development
Implementing HIPAA requires you to review about 115 pages, all vague and apparently skewed toward larger, more established companies. Also, HIPAA mostly focuses on what needs to be achieved rather than how to achieve it. That leaves smaller health technology companies, and startups in particular, overwhelmed and unsure of where to begin.
Below, we’ve outlined a step-by-step checklist for HIPAA compliance software to simplify the process for your software project.
Hire a HIPAA-proficient vendor
When you begin implementing HIPAA compliance requirements, ensure technical requirements are integrated into your core software infrastructure. Unless you’re planning on hiring in-house, you need a HIPAA-experienced vendor to make your app HIPAA-compliant.
Along with a standard NDA and other administrative precautions, you need to sign a BAA with your vendor before sharing any sensitive patient data. A BAA creates a bond of liability between a subcontractor and a covered entity or business associate, as well as guarantees the safety of personal health records.
Perform risk assessment and planning
HIPAA compliance is not something you should put on the back burner. It’s something to be factored in as early as possible. First, you should analyze whether your healthcare app will handle and transmit PHI to covered entities or their business associates. This initial assessment will tell you whether HIPAA regulations apply to your app in the first place.
HIPAA or no HIPAA, you then need to conduct a risk assessment to analyze potential threats and vulnerabilities to the confidentiality, integrity, and availability of ePHI. Once you’ve got a better sense of the potential risks, you need to develop a risk management plan in accordance with ISO 27001:2022 to outline how your solution will address the identified risks — along with a contingency plan that will detail procedures for data backup, disaster recovery, and emergency operations in case of a system failure or breach.
Implement technical safeguards
So, you’ve defined that your healthcare mobile or web app is subject to HIPAA, and general security frameworks like NIST won’t cut it. What next? Developing a HIPAA-compliant app for the healthcare industry requires a comprehensive approach covering all aspects of the HIPAA Privacy and Security Rules, plus any applicable state laws.
In the table below, you may find the most common HIPAA violations in OCR’s enforcement actions between 2020 and 2024.
| HIPAA Violation | Enforcement Actions |
|---|---|
| HIPAA Right of Access | 50 |
| Risk Analysis | 25 |
| Reviews of System Activity | 10 |
| Risk Management | 6 |
| Notice of Privacy Practices | 4 |
| Business Associate Agreements | 4 |
| Lack of Technical Safeguards | 4 |
| Audit Controls | 3 |
| Impermissible Disclosure on Social Media/Internet | 3 |
| Technical and Nontechnical Evaluation | 3 |
| HIPAA Privacy Rule Policies | 2 |
| Policies and Procedures for Responding to Security Incidents | 2 |
| Appointment of a HIPAA Privacy Officer | 2 |
As healthcare software developers, we’ll zoom in on the technical safeguards of HIPAA-compliant app development — but keep in mind that they are just one component of a broader compliance strategy.
Access control
Access restrictions enable authorized users to access the minimum necessary information needed to perform their job functions. Simply speaking, access control regulates who is authorized to see, use, or change sensitive data — and to what extent.
Our developers employ the following strategies to ensure HIPAA-compliant access controls:
- Unique user identification system (biometric access, smart keys, password, or PIN),
- Role-based access control,
- Automatic logouts,
- Strong encryption and at least two independent methods of user authentication for remote access.
Data security
Although HIPAA doesn't mention the word “encryption” explicitly, it does require organizations to ensure the integrity and confidentiality of ePHI, and data encryption is what helps you achieve that. Here's another important point: the regulations don't prescribe specific encryption methods.
For data in transit, the go-to encryption method is HTTPS (TLS), which often relies on strong data encryption standards such as AES-256 to protect sensitive information during data transmission.
Data storage
Again, HIPAA doesn’t dwell on what your database architecture must look like. Storing ePHI on a remote or on-premise server is a common practice, provided you have the necessary safeguards in place. If your application relies on cloud services for data storage and processing, it requires a HIPAA-compliant cloud infrastructure such as AWS, Google Cloud Platform, or Microsoft Azure.
☝️ Keep in mind that you must have a Business Associate Agreement (BAA) with any cloud provider that handles ePHI, as it legally binds them to safeguard the ePHI according to HIPAA regulations.
Also, make sure you have a disaster recovery plan in place to provide access to necessary ePHI during emergency conditions.
Communication methods
If your app includes messaging functionality, relying on standard SMS and email is a surefire way to violate HIPAA compliance and, in particular, the requirements for protecting ePHI in transit.
You must use only secure, encrypted methods for transmitting ePHI that may include:
- A secure link to a HIPAA-compliant portal where the patient can authenticate and access their data.
- SMS with authorization, with explicit permission from the patient.
- Secure in-app messaging (end-to-end encryption, robust user authentication mechanisms, data at rest encryption, etc.).
Logging and log management
Without robust logging and log management, you lack the verifiable evidence needed to demonstrate that your app complies with HIPAA's security and audit requirements.
Here’s what software mechanisms help set up your log management system:
- Event logs and audit trails.
- Procedures for monitoring log-in attempts and reporting discrepancies.
- Procedures to regularly review records of information system activity.
As for log content details, go beyond just the types of events for better security. You can include the specific data in logs, such as timestamps, user IDs, IP addresses, type of access, and other details to provide a more comprehensive audit trail.
Provide users control over their data
HIPAA explicitly requires covered entities and BAs to respect and facilitate patients' rights regarding their PHI. For a healthcare app, it means giving users better control over their personal health records so they can take a more active role in their healthcare.
Techwise, this translates into specific features within your app:
- Easy access to patients’ complete medical records that allows them to view, access, and download their data in common formats such as PDF and HL7.
- A clear pathway for users to ask for amendments to their health information.
- A readily accessible log of who has accessed their data and when.
- The ability for users to easily transfer their health data to another provider or health plan.
Provide ongoing maintenance and updates
A holistic compliance strategy isn't just a “set it and forget it” process. Even after you’ve embedded each and every safeguard measure, it’s crucial to continuously monitor your healthcare software for compliance with HIPAA and apply security standard updates and patches.
HIPAA сompliance for AI healthcare apps
Today, 94% of healthcare companies leverage AI/ML to some extent. Your healthcare tech solution is also likely to employ artificial intelligence to automate some processes or personalize patient experiences. While AI can equip your healthcare solutions with unique and competitive capabilities, training your AI on PHI can also expose you to significant HIPAA compliance concerns.
- Authorization — Using PHI for AI training often falls outside the TPO (Treatment, Payment, or Healthcare Operations) use, which requires you to get patient authorization. Securing authorization from large numbers of patients is a tall order.
- Data minimization — HIPAA's "minimum necessary" standard requires using only the minimum PHI needed. This standard runs counter to the data-intensive nature of AI training.
- Role-based access — Integrating AI introduces new roles and access controls, which can be problematic for smaller companies, and startups in particular, where you need to grant PHI access to AI-focused employees who typically don't work with such data.
Unfortunately, artificial intelligence evolves faster than regulatory frameworks, so there are no clear-cut HIPAA rules for AI's use of patient data. HIPAA's message is clear, though: protect patient data at all costs.
Our AI developers typically draw upon the FTC's focus on consumer protection and the National Institute of Standards and Technology AI Risk Management Framework (AI RMF) to add another AI-specific layer of security to AI-enabled healthcare applications, ensure their compliance with healthcare regulations, and reinforce a responsible approach to AI development in healthcare.
How much does building HIPAA-compliant software cost?
It’s difficult to pin down a specific number for HIPAA compliance application development, as the cost can vary greatly depending on multiple factors.
- The scope and complexity of your application — the more features your app is kitted out with, the more complex and resource-demanding it’ll be to ensure each one is HIPAA compliant.
- Data handling — if your application processes troves of sensitive data, it’ll require more robust security measures.
- Advanced technologies — as we’ve mentioned earlier, the implementation of AI and such requires your development team to implement specific security measures.
- Integrations — integrations can also contribute to the complexity of the development processes as they add multiple points of vulnerability to the system.
- Security infrastructure — HIPAA allows for some level of flexibility, recognizing that smaller companies aren’t able to allocate the same resources and risk profiles as larger organizations. So, the complexity of your software’s security infrastructure can vary, which is reflected in the development costs.
- Maintenance and updates — is your company able to continuously monitor your app and systems for compliance with HIPAA, or do you need a third-party vendor to take over this process? Costs will vary based on your answer.
In our experience, the cost to develop HIPAA-compliant healthcare applications ranges from $35,000 to $250,000. There's a lot of fluctuation, so we recommend contacting our company for a personalized estimate to help you plan your budget.
Orangesoft’s experience in HIPAA-compliant app development
As a software development company specializing in healthcare, we wrangle with HIPAA compliance in almost every healthcare-related project. It's a complex landscape, with evolving regulations and unique challenges for each project.
For example, when developing a web platform for medical staff and a complementary mobile app for post-stroke patients, our developers solved a number of unique challenges related to HIPAA compliance, such as:
- Making sure the PHI stored on patients' mobile devices (which is outside the covered entity's direct control) is protected.
- Limiting the PHI stored on the mobile app to only what is absolutely necessary for its intended purpose.
- Securely syncing data collection between the mobile app and the web platform.
- Ensuring end-to-end encryption for all communication modes, including video, audio, and messaging, within the telemedicine capability, and many other challenges.
Working in collaboration with our client’s team, we successfully implemented all necessary safeguards and measures to ensure full HIPAA compliance for the web platform and mobile app, enabling our client’s team to deliver secure, effective care.
HIPAA compliance is just the tip of the regulatory iceberg
While many companies have concerns regarding HIPAA compliance, the truth is that it only sets a minimum floor for the protection of PHI. If you’re developing for the U.S. market, you’ll likely need to navigate state and federal privacy protections, such as the FTC Act and 42 CFR Part 2, which may either supersede HIPAA or add layers of complexity and stricter standards.
Whatever regulatory spectrum you’re on, you must prioritize the security of your healthcare software by implementing best practices to minimize non-compliance risks.
If you need help with developing a HIPAA-compliant app, the Orangesoft team is a click away. Contact our team for more information on HIPAA-compliant application development.
