With their rich longitudinal and real-time patient data, medical devices have long become indispensable to the healthcare industry. But without medical device integration (MDI), data from wearable sensors, diagnostic tools, and therapeutic equipment remains locked within the source, with zero chance of improving patient outcomes.
To integrate real-time patient data with electronic health records and help clinicians reduce manual data entry, medical devices need to be plugged into a broader healthcare tech ecosystem. That’s exactly what we’ll focus on in this article: how to integrate a medical device and do it right.
Key takeaways
- Medical device integration is integral for more informed clinical decision making and improved patient outcomes, with potential benefits for the entire health system.
- Successful integration links various medical devices, middleware, and healthcare systems using standardized communication protocols and data formats.
- Ways of achieving such integration vary, with regulatory requirements, data security, and interoperability nuances shaping both the architecture and implementation strategy.
What is medical device integration (MDI)?
Medical device integration is the process of connecting medical hardware and software systems, including patient monitors, infusion pumps, ventilators, and electronic health records, to share and analyze critical health data in real time.
Core components of medical device integration include:
- Devices — IoT sensors, wearables, and legacy medical devices like patient monitors and ECGs.
- Integration engines — middleware like Redox and Rhapsody.
- Destination sources — electronic medical records, analytics dashboards, AI models.
How medical integration works:
- The medical device picks up data.
- An integration layer (the device’s software or vendor-provided interface) translates that data into standard formats.
- Middleware routes that data, using HL7, FHIR, or DICOM standards.
- Connected systems fetch and act on that data — for example, an EHR auto-fills vitals.
Technical foundations of the device integration process
The fluency and speed of medical data interaction directly hinge on how well devices can communicate, the way that data is structured, and its path into the clinical system. Meeting these requirements requires a solid technical basis.
Communication protocols
Regardless of the data type sent, a medical device needs the right communication protocol to transfer the data. The choice is made based on the device’s function, environment, and the manufacturer's design approach.
Here are common communication protocols and standards that support seamless medical device integration:
- Bluetooth Low Energy (BLE) — a standard choice for wearables like glucose monitors and patches, because it’s ultra-low-power and gives patients freedom to move.
- Wi-Fi — often used to loop in high-bandwidth devices like medical imaging equipment and video-enabled devices. The protocol supports high throughput and low latency but relies on stable network infrastructure.
- USB — a versatile connector standard usually applied to point-of-care devices. It’s designed for plug-and-play, enables high-speed data transfer, and makes sure vital patient information is communicated fast and securely.
- MQTT — a lightweight, publish-subscribe messaging protocol used for communication between devices and cloud-based healthcare platforms. MQTT 5.0 supports QoS levels, which make sure that each message is delivered exactly once, making this protocol a good match for real-time remote monitoring in healthcare.
- REST APIs — a proven method for healthcare system integration. REST APIs power stateless, secure HTTP/HTTPS communication between devices and backend systems like EHRs.
Usually, developers combine communication technologies to fit different parts of the data journey.
💡All nodes of the communication channel must be encrypted with TLS 1.3 to protect sensitive medical data from interception or tampering.
Data transfer formats
Healthcare systems feed on structured data. However, medical device data is unstructured or semi-structured by default, with different manufacturers using different labels for their data. Even the same type of data can show up in a different format, terminology, or measurement unit across device manufacturers.
That’s why developers put middleware or integration engines as an in-between layer to transform the device’s raw or proprietary data into a standardized format. Data mapping, normalization, and validation — all happen right within this layer.
Here are the most common standardized formats for device data transformation:
- HL7 v3 — Although it’s in the phase-out stage, many hospital environments still rely heavily on it for clinical messaging within inpatient and legacy settings.
- FHIR — As a successor to HL7 v2, FHIR is skewed towards newer applications, cloud platforms, and mobile health. It uses web-native formats such as JSON/XML and REST APIs.
- DICOM — DICOM is an international standard for medical imaging data. The standard sets up a bridge between imaging devices and Picture Archiving and Communication Systems/AI-based diagnostics platforms.
- IEEE 11073 — The ISO/IEEE 11073 standard family supports plug-and-play interoperability for consumer-grade medical devices. It paves the way for seamless data exchange between personal health devices and healthcare systems.
Integration modes: real-time vs. batch integration
Different healthcare systems require different data velocity. Data from a bedside monitor must flow into an EHR in near real-time, while other systems can get by with uploading step counts or glucose levels once a day.
- Real-time data integration comes into play when seconds can make a difference, which is usually the case in intensive care units, emergency medicine, and sensitive remote monitoring environments. Real-time data integration is powered by low-latency communication protocols such as MQTT or WebSockets and often demands edge processing. Always-on device connectivity, message brokers or publish-subscribe architectures, data buffering and retry mechanisms, and efficient serialization formats also stand behind this integration mode.
- Batch integration is the way to go when the system can tolerate some latency and needs only periodic updates. Devices often store data locally and send it at defined intervals over HTTPS or RESTful APIs. Scheduled data pushes, local data caching, data compression, and retry logic for when the device is offline are the core tech differentiators of this integration mode.
Middleware and gateway architectures: edge vs. cloud
Depending on the clinical setting, device capabilities, and data sensitivity, middleware can be deployed in a cloud environment (such as Redox or AWS HealthLake), in an on-premise/edge box, or use a hybrid model that merges both.
- Cloud integration — Hosted on platforms like AWS, Azure, or GCP, cloud middleware is suitable for aggregating troves of sensor data, running AI/ML models, and performing longitudinal analysis at scale. Cloud-enabled architecture is well-suited for use cases such as remote monitoring, population-level trends, and predictive insights. On the downside, latency, bandwidth constraints, and potential compliance setbacks make it less fit for offline environments or real-time clinical intervention.
- Edge integration — Deployed on-premise, edge middleware is for when the device data needs to be processed with minimal latency and locally. It’s the preferred approach for ICUs, ERs, and point-of-care systems, where real-time processing and local reliability are must-haves. If the internet connection is lost, edge devices will keep functioning locally.
- Hybrid approach — In most cases, it’s not an “either-or” deployment. When it comes to connected medical devices, the hybrid approach is the most popular option as it allows healthcare organizations to process time-sensitive data at the edge while handing over heavier analytics and storage to the cloud.
What are the challenges of medical device connectivity? 2026 edition
Medical device connectivity is a $3.38 billion market, which is expected to surpass $17 billion by 2034. But as the demand for medical device integration services ramps up, so do the challenges of making it work in an environment known for its rigid constraints.
Fragmented device ecosystems with proprietary protocols
Interoperability between different device manufacturers is the classic villain: there’s an average of 10 to 15 connected devices per patient bed, with different devices using unique, closed communication standards. Healthcare providers end up with islands of technology that prevent data aggregation for predictive analytics and other clinical uses.
Common ways of addressing these challenges include complex adapters, custom code, or interface engines that convert proprietary data formats into standardized ones like HL7, FHIR, or JSON. Yet, even these workarounds don’t fully eliminate semantic mismatches related to units, field names, and time formats.
Interoperability limitations across legacy and modern systems
Even if you translate that device data, systems may still struggle to leverage it because of the system-level differences. There’s a Tower of Babel-like situation at the hardware and protocol level where legacy devices like bedside monitors talk over legacy interfaces like RS-232, while modern IoT wearables go with web-native standards such as FHIR over HTTPS or MQTT.
As a result, many hospital tech teams are stuck writing regex just to find patterns, like scanning for "|ERR|" flags in HL7 logs. Long-term, what they can really benefit from is solid middleware or an integration engine to bridge the gaps.
Luckily, by 2026, regulatory mandates are expected to accelerate the change towards easier interoperability, with such initiatives as the CMS Final Rule and MDR v3 pushing the adoption of modern standards like FHIR and phasing out legacy protocols.
Making sure the data semantics stay consistent
As we mentioned earlier, no adapter or interface engine can guarantee the unified semantics of medical data across medical devices. Even such simple fields as “SpO2” or “Temp” can vary in units, frequency, or format based on the manufacturer. The lack of uniformity can lead to critical patient data being lost in translation for EHRs, dashboards, and AI models.
That’s why pure syntactic conversion is not enough. Integration platforms must also perform semantic and structural transformation on medical device data, including unit harmonization, time normalization, and data validation, such as range checks and missing values.
Security, consent, and regulatory friction
Oftentimes, medical device integration may lead to additional regulatory oversight. For example, if the functionality of the medical device integration software goes beyond data transfer and display, it’s considered a Medical Device Data System and is subject to potential 510(k) clearance.
In the EU, the matter is even more complicated. Any middleware or integration layer that interprets, transforms, or acts on data may fall under Class IIa or higher, triggering CE-marking requirements and a formal conformity assessment.
Security and consent considerations add another layer of complexity. According to regulatory guidelines, any integration layer that handles sensitive patient data requires a set of robust safeguards like data encryption, access controls, and others. If the PHI data crosses borders, healthcare organizations must also address cross-jurisdictional compliance obligations. And let’s not forget the critical need for clear, explicit patient consent.
Regulatory and compliance considerations
The legal aspect of integrating medical devices remains one of the most ambiguous elements of the equation. Because today’s devices blend hardware, software, and data in ways that sometimes run counter to traditional classifications, MDI often ends up in a gray zone of overlapping regulations.
Difference between “data consumers” and “SaMD” in regulatory pathways
Regulatory bodies don’t apply the same rules to all software. So, before checking whether they need a 510(k) submission, CE marking, or anything else in the first place, healthcare organizations and developers need to determine what the integration layer actually does to understand the category it goes into.
In this respect, the integration software can either land in the data consumer category or fall on the spectrum of software as a medical device.
Data consumers
Data consumers are systems and applications that receive and use medical device data but do not tweak, make sense of, or act on the data in a way that impacts patient outcomes. These solutions don’t carry the healthcare regulatory obligations of SaMD, but are still subject to data privacy and cybersecurity regulations like HIPAA and GDPR.
Software as a medical device
Software as a Medical Device (SaMD) is a software category that performs medical functions on its own, without being part of the hardware. In simple terms, if an integration platform runs analysis on medical device data or if the middleware sifts out or triages that data based on clinical thresholds, it crosses the line from being a passive data conduit into being a clinical tool.
It also means that the regulatory landscape of the integration software solution becomes as complex as that of SaMD.
| Key difference | Data consumer | SaMD |
|---|---|---|
| Role | Transmits, stores, or displays data (no clinical logic) | Analyzes or acts on data |
| Regulatory category | Usually non-medical | Regulated as a medical device |
| Associated risk | Low | Medium or high |
| Compliance requirements | HIPAA, GDPR | MDR, FDA SaMD guidance, ISO 13485, QMS |
| Example | EHR viewer, archival system | Real-time alerting, dosing calculators |
HIPAA, GDPR, and FDA requirements for integrated systems
As mentioned above, when the integration software does more than transport data, like flagging anomalies or triggering intervention, it’s classified as regulated device software.
In the US, this could mean:
- Classification as a Medical Device Data System (MDDS) or Software as a Medical Device (SaMD) under the FDA.
- The need for 510(k) submissions if the integration has an impact on clinical workflows and decision-making.
- Adherence to 21 CFR Part 820 in terms of quality controls and risk management.
- Implementation of end-to-end data safeguards such as access controls, audit logging, encryption, and others, if the integration platform deals with Protected Health Information (hence falling under HIPAA requirements)
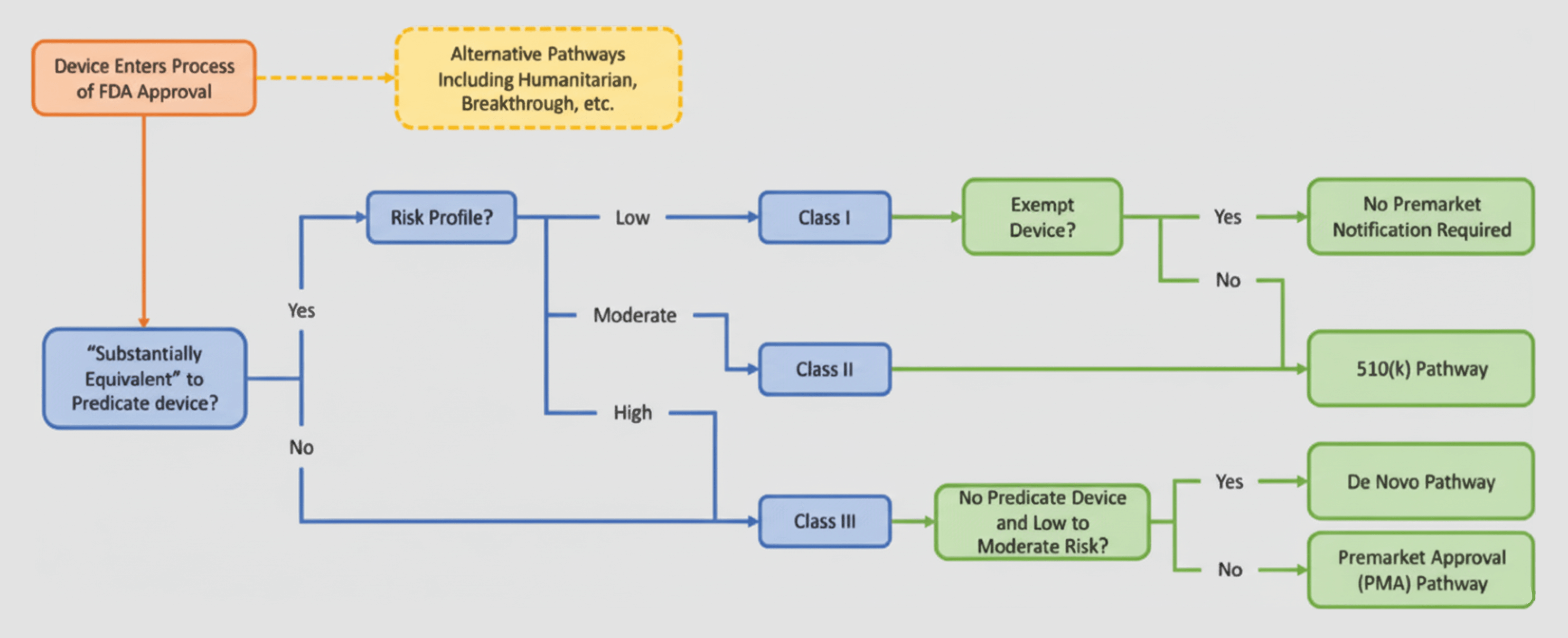
In the EU, this could mean:
- Reclassification under the Medical Device Regulation (MDR) that can put the integration software into Class IIa or higher, which entails CE marking, clinical evaluation, and post-market surveillance.
- Full compliance with the General Data Protection Regulation (GDPR), including data minimization, purpose limitation, and other obligations, if the integrated device handles Personally Identifiable Information (PII) and health-related data.
| Medical device classification | Risk | Device type/ Duration of use | Assessment requirements |
|---|---|---|---|
| Class I | Low | Non-sterile Noninvasive | Self-certification/Self declaration Technical documentation is required |
| Class Is | Low | Sterile Noninvasive | Notified body Review of technical documentation and limited QMS (Annex IX), or product conformity verification (Annex XI) |
| Class Im | Low | Measuring function Noninvasive | Notified body Review of technical documentation and limited QMS (Annex IX), or product conformity verification (Annex XI) |
| Class Ir | Low | Reusable Noninvasive | Notified body Review of technical documentation and limited QMS (Annex IX), or product conformity verification (Annex XI) |
| Class IIa | Medium | Invasive Short term | Notified body Review of technical documentation and full QMS (Annex IX), or product conformity verification (Annex XI) |
| Class IIb | Medium to High | Invasive or active Long term | Notified body Review of technical documentation and full QMS (Annex IX), or product conformity verification (Annex XI) |
| Class III | High | Invasive or active Long term | Notified body Review of technical documentation and full QMS (Annex IX), or type-examination (Annex X) and product conformity verification (Annex XI) |
Implications of IEC 62304 and ISO 13485 for integration components
Once your integration software is in the regulated territory, regulatory bodies expect you to follow certain best practices related to the design, development, and lifecycle management of medical software. Two of the most critical standards are IEC 62304 and ISO 13485.
IEC 62304: Software lifecycle and risk management
IEC 62304 lays out a defined framework for managing the software lifecycle end-to-end. For integration layers, this helps:
- Keep tabs on the changes across device drivers, APIs, and processing logic
- Systematically handle updates to standards like FHIR or HL7
- Address risks related to timing, data loss, or misrouted data
ISO 13485: Quality management of integration software
ISO 13485 is the internationally recognized quality management benchmark for medical device systems, including middleware or gateways integrated into a medical system. When applied to integration components, ISO 13485 provides the structure for:
- Better documentation and traceability
- Explicit roles and review processes during development
- Organized validation and release procedures
💡 Even if the middleware you’re developing isn’t considered a regulated medical device, applying the ISO 13485 standard still helps de-risk your solution, especially when it connects to downstream tools that are regulated.
Data harmonization and normalization strategies
If a medical device company can clear the costly headache of multi-device integration, it’s not just fixing a garden-variety industry issue — it’s removing one of the perennial roadblocks for healthcare professionals. Taking care of the apples-to-oranges data problem is a core enabler on the way to interoperability across devices and systems.
Dealing with inconsistent units, formats, and timestamping
As we’ve mentioned earlier, every device manufacturer has their own idea of unit and format standards. Timestamps also come in every flavor, showing up as ISO, epoch, or local time with no zone info.
To clean this up, you’ll need:
- A unit normalization layer (e.g., always convert to SI units)
- Format converters to map vendor payloads to a common schema
- Timestamp reconciliation with proper timezone handling
- Rules to catch missing or malformed fields before they hit downstream logic
It’s impossible to get reliable results from analysis tools or initiate alerts without bringing the data into a unified view. It’s plumbing, but it’s critical plumbing.
Normalizing device data for longitudinal tracking and analytics
Once those individual data points are cleaned and converted to a common format, they need to be lumped together and made usable over time and across patients and locations. This is what we call longitudinal tracking normalization.
You’ll need to:
- Map synonymous labels (such as SpO2, O2Sat, oxygen_saturation, and others) to a unified field
- Align sampling rates and interpolate where needed for trend accuracy
- Use consistent field names and data types across device families
- Apply event deduplication and synchronization to get rid of data overlaps
- Standardize timestamps to a shared reference (like UTC) so trends remain accurate across time zones and system boundaries
In practice, you’ll build a robust translation layer that’s resilient to vendor quirks and designed for scale. A translation layer often goes into your abstraction layer.
Building a device-agnostic abstraction layer
Speaking of the abstraction layer, it has to be vendor-agnostic by design. The main idea behind it is to normalize all incoming data as closely as possible to the source before it enters the core system. Each device funnels data through an adapter that maps it to a canonical internal format (e.g., open standards like FHIR). This way, all vendor-specific quirks are left behind at the boundaries, while the core logic, APIs, and downstream systems deal with just one internal representation.
As for adapters, keep them simple, limiting their role to translating and forwarding the normalized data.
Ensuring data security and patient privacy at every touchpoint
One report discovered 162 vulnerabilities across connected medical devices in 45 healthcare organizations. Whether it’s due to legacy systems, unencrypted traffic, or a lack of built-in security by design, virtually any medical device may introduce vulnerabilities into the healthcare tech system that can compromise patient safety.
To keep data security at the highest level, integration teams need to embed safety nets at every layer of the integration stack:
- Secure device-to-app communication — Encrypting all data in transit, applying secure pairing protocols, and device identity verification.
- Strong authentication and authorization — Using robust, standards-based frameworks like OAuth2 and PKI to limit data access.
- Privacy-preserving architecture — Designing for data minimization, enforcing least-privilege access, and isolating devices from critical infrastructure.
From what we’ve seen, sticking to the privacy-by-design principle, such as baking data minimization and least-privilege access into the architecture early on, helps integration teams skip costly rework associated with retrofitted privacy controls and compliance issues down the road.
4 battle-tested tips for successful medical device integration from Orangesoft
Medical device integration sounds simple on paper, but in reality, it’s anything but. As a healthcare software development company with 15+ years of experience, we’ve learned that regulatory requirements, diverse medical devices, scalability considerations, and numerous other challenges can throw a wrench into the integration process or disrupt it entirely. Here are three tips that can at least save you from bigger surprises:
Involve regulatory and QA teams early
When compliance gets pushed to the end of the project, the team has to overhaul the entire solution to adjust it to the FDA, MDR, HIPAA compliance, and other regulatory guardrails. What we typically do is we loop in regulatory and QA teams right from the very start. They help the integration team define how the system needs to be built, what data must be encrypted, what activities should be documented, and how things should be tested.
Give a deep clinical perspective a seat at the table
Deciding on data formats and transport protocols is one thing. But making sure that the integrated systems support clinical workflows requires insights from healthcare professionals who work with the integrated data. The integration team can build upon the insights to prioritize data points, alert thresholds, user interfaces, and interoperability features.
Design for device obsolescence and backward compatibility
If your integration architecture isn't built with obsolescence in mind, you'll find yourself rewriting core components each time vendors change protocols or new standards come into play. That’s why we recommend designing loosely coupled systems with abstraction layers between the device interface and the core application logic.
This way, developers can switch or upgrade individual components without breaking the entire system. Backward compatibility is also something we always factor in to make sure the integration can handle legacy devices.
Always prototype with real hardware and edge cases
Using actual devices as prototypes (not just simulators or mock data) gives your team a sneak peek at how the system will work in real clinical scenarios. Such early, hands-on testing uncovers everything from hardware-specific bugs to edge cases and data inconsistencies before the deployment.
We also recommend curating a library of edge cases, such as disconnected devices, dropped packets, and incorrect data formats — and building tests around them.
Medical device integration success is a team effort
The main idea we’ve gleaned from medical device integration projects is that it’s never a purely technical exercise. It’s an iterative, continuous, and collaborative process that merges clinical needs, regulatory landscapes, and evolving technologies.
If you need a reliable medical device integration partner with a proven track record, Orangesoft is ready to help. We have a team of senior developers, solution architects, and QA specialists with firsthand experience in FDA, MDR, HIPAA, FHIR, and HL7 compliance, as well as deep technical knowledge in integrating different medical devices. Book a free consultation with our senior healthcare engineers.
